Article
Feb 4, 2025
Cutting Through the Noise: EDR, XDR, MDR, and SIEM Explained
Is AI automation really more efficient than manual work? We break down the costs, time savings, and long-term benefits of AI-driven processes compared to traditional methods to help you make an informed decision.
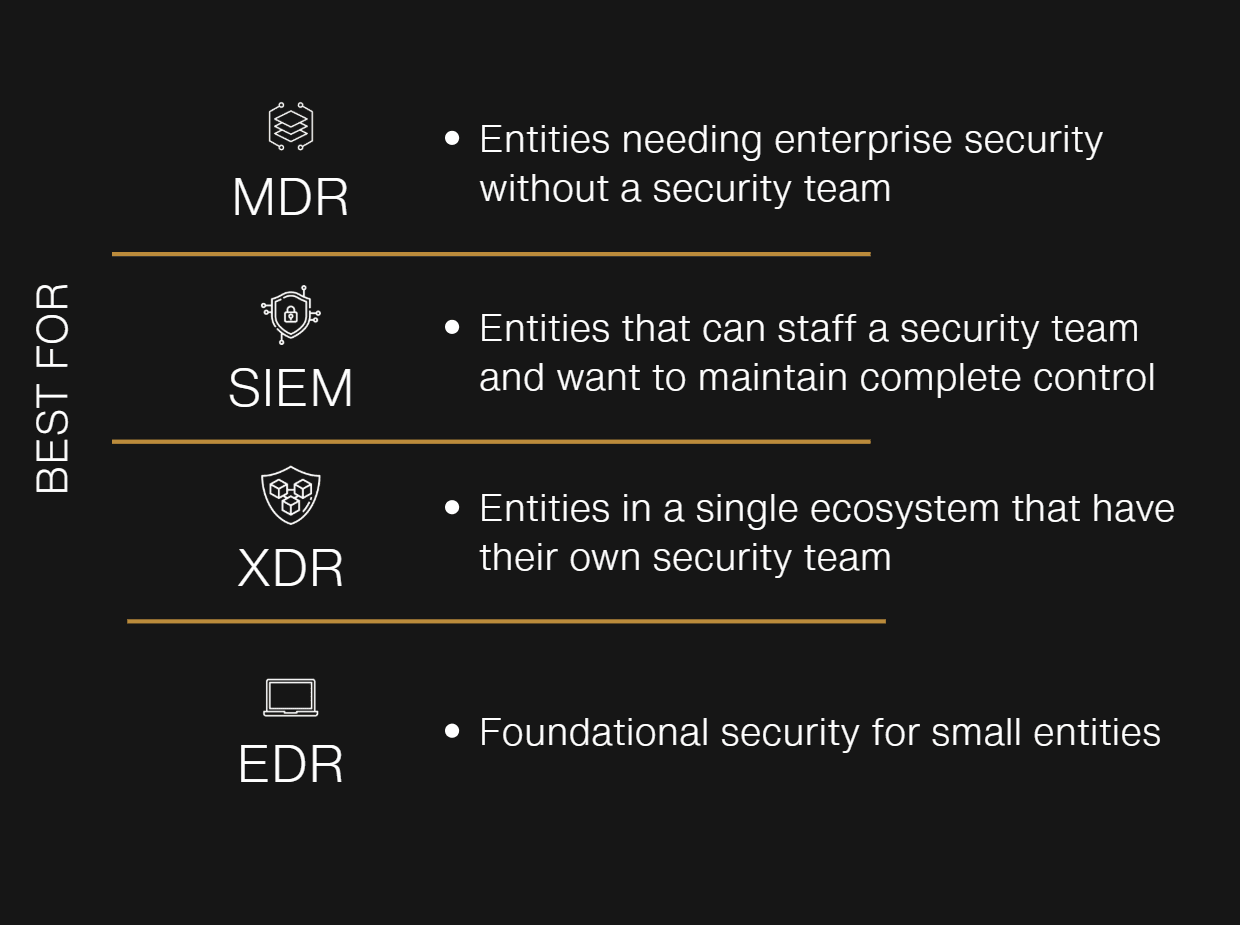
EDR
Endpoint Detection and Response
Security focused on endpoints (laptops, servers, mobile devices). Detects malicious activity and gives tools to investigate/respond.
✅ Advantages | ❌ Disadvantages |
|---|---|
Strong visibility into device specific attacks | Limited to endpoints (no email, cloud, or identity visibility) |
Provides strong basic level security for organizations | Visibility / detections can vary greatly between vendors |
Behavioral detections may require some expertise to confirm |
XDR
Extended Detection & Response
Evolving from EDR that integrates multiple security datasets to include endpoint, identity, cloud, and network into a single platform.
✅ Advantages | ❌ Disadvantages |
|---|---|
Unified visibility across different attack surfaces | Usually heavily tied into a single vendor’s ecosystem |
Helps reduce false positives by through correlation of multiple datasets | Less flexible than a SIEM (think “walled garden”) |
May need analysts to interpret detections or configure |
MDR
Managed Detection & Response
A managed service (often built on top of EDR/XDR tooling) where a provider monitors, investigates, and responds to security detections on behalf of your team.
✅ Advantages | ❌ Disadvantages |
|---|---|
24/7 monitoring without need for security personnel | Outsourced detections (great for small teams) |
Faster incident response & with expert analysts | Quality and tooling varies widely between MDR providers |
Cheaper than hiring hiring internal team | Not all integrations are accepted by all MDR providers |
SIEM
Security Information and Event Management
A centralized platform that ingests and analyzes logs from multiple datasources to include endpoint, cloud, firewall, etc. This platform is much more customizable than XDR and includes custom detection capabilities.
✅ Advantages | ❌ Disadvantages |
|---|---|
Broadest visibility - you can log virtually anything | Manual setup and tuning effort, will need security expertise |
Highly customizable for detections, reporting, and querying | Some detections out of the box but will need tuning |
Typically needed for any business that needs compliance | Will grow with data volume and can become costly |
*DR
Other Detection and Response
Other Detection & Response platforms to include Cloud Detection & Response (CDR), Network Detection & Response (NDR), and Identity Threat Detection & Response (ITDR) are more specific solutions for their attack surface
✅ Advantages | ❌ Disadvantages |
|---|---|
Highly specific detections for their attack surface | Sometimes bundled into XDR platforms and are no longer add-ons |
Detects misconfigurations along with suspicious activity | Need to insure that it integrates with current security stack |
May begin to overlap with other tooling that you pay for |
Forging Your Path
Businesses evolve and so do your threats. As the business expands your security stacks needs to evolve with it. Where you begin today won’t be where you need to be tomorrow.